Bandit 0 - 12
OverTheWire: Introduction
Starting from level 0, each level introduces new challenges, guiding players on how to advance their skillset step by step throughout the game. My tech notes will provide practical solutions, tips, and explanations in order to help others underatand the command line, troubleshoot issues, and improve problem solving skills. Referencing material while learning is never a bad idea, it will help reinforce and recitate on important fundamentals that will be useful in the future. Navigating computers using the command line is essential in tech fields such as cybersecurity, programming, and system administration.
- Efficiency: faster than using the GUI, scripts can be used to save significant time.
- Control: greater access and additional ways to manipulate files, system processes, and configurations.
- Resources: CLI is more lightweight than GUI, uses less sytem resources, and is essential for automation tasks.
https://overthewire.org/wargames/bandit/
SSH Information: Host = bandit.labs.overthewire.org Port = 2220
Level: 0
This level requires the user to connect to a remote server using SSH over port 2220. Given to use, we have the username bandit0 and password bandit0. The command I used to proceed: ssh bandit0@bandit.labs.overthewire.org -p 2220
Commands Used:
- ssh (Secure Shell) - Used to securely connect to the Bandit server, usual port is 22. Insecure version is Telnet (23).
- ls (List) - Useed to list files and directories in the current directory. Useful for finding available files & data.
- cat (Concatenate) - Used to display the contents of a file, in this case revealing the password for the next level.
Note: it is best practice to operate as a regular user for tasks like connecting to a remote server. Only elevate with sudo when needed for specific administrative tasks.
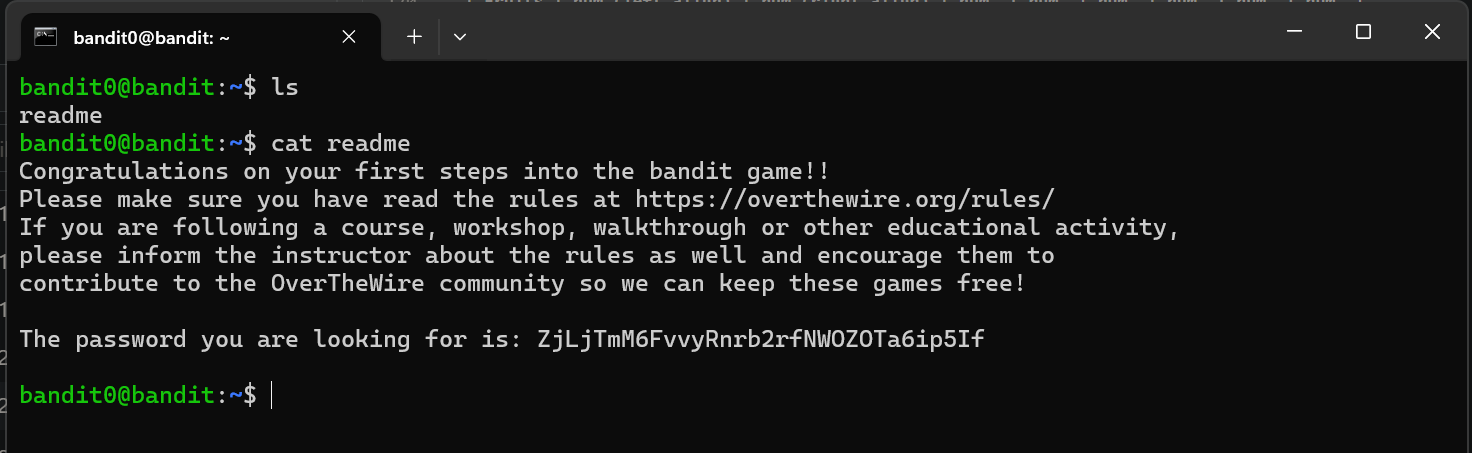
Level Password: ZjLjTmM6FvvyRnrb2rfNWOZOTa6ip5If
Level: 1
The password for the next level is stored in a file called - located in the home directory
Notes:
- In future levels, you may encounter files with names starting with a dash. This can cause issues, as commands often interpret the dash as an option (for example, ls -a)
- Options - also known as a flag or switch, is a way to modify a command to alter its output.
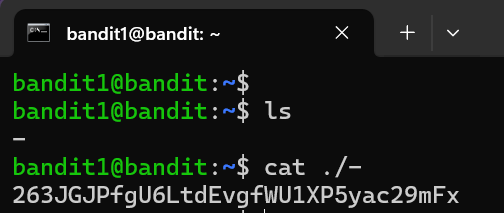
Level Password: 263JGJPfgU6LtdEvgfWU1XP5yac29mFx
Level: 2
The password for the next level is stored in a file called spaces in this filename located in the home directory
Notes:
- The file name contains spaces, you must enclose the file name in either single or double quotes to ensure the command interprets it as a single item rather than seperate arguments.
- Tab key enables auto completion when typing commands, file names, or directory paths. This way you can finish typing quickly & accurately.
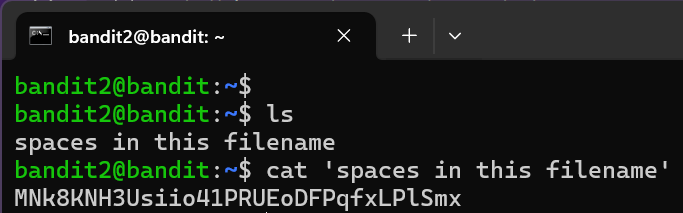
Level Password: MNk8KNH3Usiio41PRUEoDFPqfxLPlSmx
Level: 3
The password for the next level is stored in a hidden file in the inhere directory.
Commands:
- cd (change directory) this command is used to navigate between directories by moving to different locations within the file system.
- ls -a (list all) - this tells ls to list all files, including hidden files (such as those starting with a dot ‘.’)
Level Password: 2WmrDFRmJIq3IPxneAaMGhap0pFhF3NJ
Level: 4
The password for the next level is stored in the only human-readable file in the inhere directory.
Commands:
- file - tells the system to examine the specififed file, in this case all files in this directory * and attempt to classify them by types.
- ‘’ the astericks is a wildcard that matches all files in this directory. By combining this with ./ (current directory) we find all files in the current directory ./
- ASCII - in this example, this is the only human readable file in the inhere directory.
Level Password: 4oQYVPkxZOOEOO5pTW81FB8j8lxXGUQw
Level: 5
The password for the next level is stored in a file somewhere under the inhere directory and has the following properties: human-readable, 1033 bytes in size, not executable
Commands:
- find used to search for files and directories based on a criteria such as name, type, size, permissions, and more. syntax: find [path] [criteria] [action]
- options used: -type f = regular file, -size 1033c which is 1033 bytes,
Level Password: HWasnPhtq9AVKe0dmk45nxy20cvUa6EG
Level: 6
The password for the next level is stored somewhere on the server and has all of the following properties: owned by user bandit7, owned by group bandit6, 33 bytes in size
*Command Explanations
- / slash / key it means to search the entire server. The / is the root directory, similar tot he C: drive on Windows.
- . this represents the current directory
- ** * ** this will match zero or more characters in filenames or directory names, such as all files with *.txt extension.
- > this is a redirection operator, it will be used to redirect the output of a command to another file or location rather than on the current screen.
- 0 by placing a zero before the redirection operator, it will target standard input: this is useful when automating since you can feed commands with data from files.
- 1 by placing a zero before the redirection operator, it will target standard output: this is regular successful output displayed on the screen.
- 2 by placing a zero before the redirection operator, it will target standard errors: this can be used to filter or view error messages seprarately.
Notice: when we typed in the command: find / -user bandit7 -group bandit6 -size 33c, there will be many error messages saying ‘permission denied’. 
Referring to what’s mentioned above, we must suppress error messages by redirecting them to a special location for hiding them from the output.
Directories
- /dev Device Directory: can be seen as a toolbox of special files, representing devices and system interfaces rather than traditional files. The operating system and users can use these files to interact with hardware, virtual devices, and system resources.
/null can be seen as a tool within the directory to dispose of data and manage data flow by discarding unwanted output or errors.
- /dev/null combined: they form a special file that acts as a “black hole” for data.
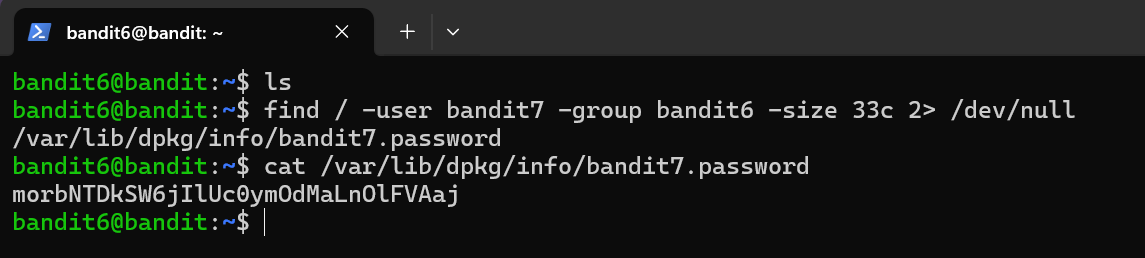
Level Password: morbNTDkSW6jIlUc0ymOdMaLnOlFVAaj
Level: 7
The password for the next level is stored in the file data.txt next to the word ‘millionth’
Commands:
- grep - Global Regular Expression Print: CLI tool used to search for text searching, pattern matching, file filtering, data analysis, and script automation. In this example, we are telling grep to search for the word ‘millionth’ in the file: data.txt which can be found in the current directory. Grep = search for pattern in file.
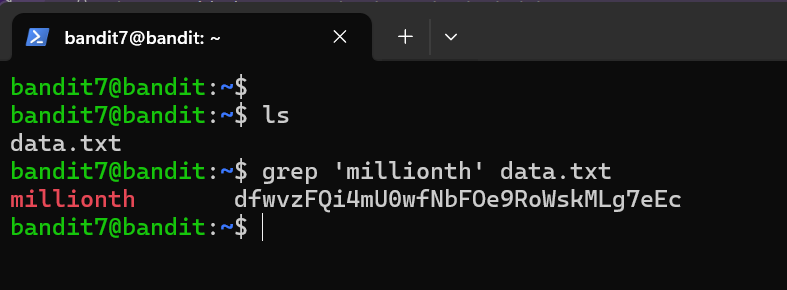
Level Password: dfwvzFQi4mU0wfNbFOe9RoWskMLg7eEc
Level: 8
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
Commands
- sort - sorts the contents of a target file alphabetically
- uniq - ‘unique’ alone this filters out consecutive duplicates, leaving only unique entries. option -u > tells uniq to only print lines that appear exactly once.
** ** - ‘pipe’ - takes the output from a previous command and passes it as input to the next command, so you can chain commands together
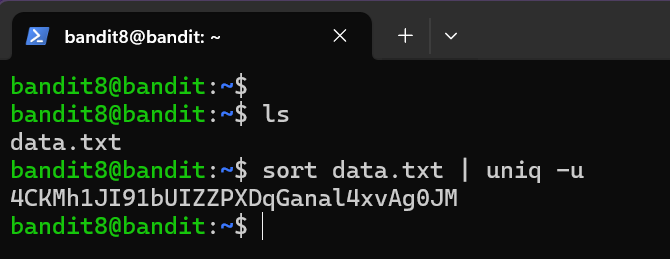
Level Password: 4CKMh1JI91bUIZZPXDqGanal4xvAg0JM
Level: 9
The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several ‘=’ characters.
Commands
- strings tool used to search throgh binary files and extract readable text such as during times when trying to find hidden useful information in non-text files.
- option: -e s > encoding option with s for 7-bit ASCII, specifies the string should interpret the text as 7-bit ASCII, filtering out non-readable characters.
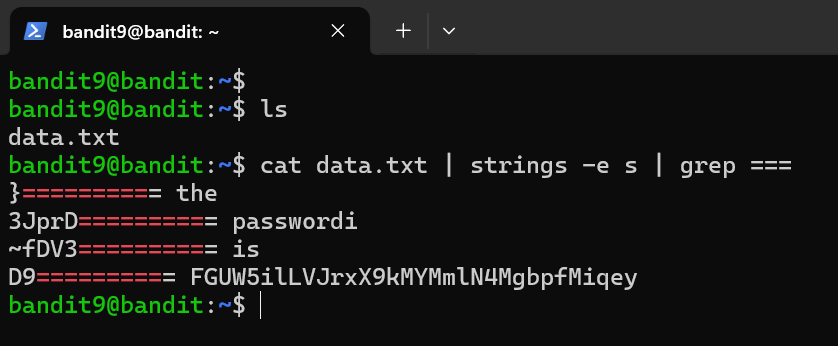
Level Password: FGUW5ilLVJrxX9kMYMmlN4MgbpfMiqey
Level: 10
The password for the next level is stored in the file data.txt, which contains base64 encoded data
Commands
- base64 this command will convert binary data into an ASCII string (A-Z, a-z, 0-9, +, and .) Base64 encodes every 3 bytes into 4 ASCII characters.
- option: -d - decodes Base64 encoded data back to its original format.
- –help , this displays a help message with summary of all options available for any given command (base64 –help)
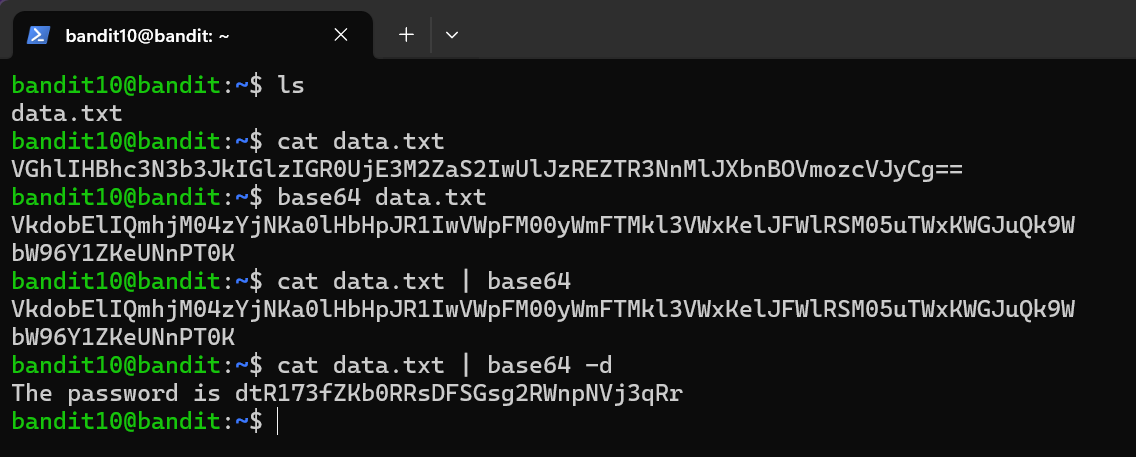
Level Password: dtR173fZKb0RRsDFSGsg2RWnpNVj3qRr
Level: 11
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
Commands
- tr - translate: used for translating, deleting, and compressing characters for text manipulation and text processing.
- ROT13 - this is a substitution cipher that shifts each letter by 13 places, often used to obscure text.
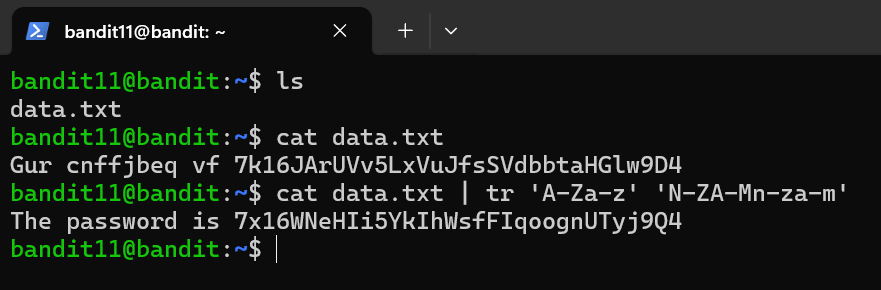
Level Password: 7x16WNeHIi5YkIhWsfFIqoognUTyj9Q4
Level: 12
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work. Use mkdir with a hard to guess directory name. Or better, use the command “mktemp -d”. Then copy the datafile using cp, and rename it using mv.
Commands
- head - (header) view the first lines of a file
- mkdir - (make directory) on this level, we created a new directory named purple inside the /tmp directory
- cp - (change directory) copies files or directories,
- mv - (move/rename) moves or renames files or directories
- rm - (remove) delete files or directories.
- xxd - (hexdump converter) convert between binary and hexdump formats.
- gunzip - (gzip decompressor) helps with handling .gz files, decompresses data.gz to data
- bunzip2 - (bzip2 decompressor) helps with handling .bz2 files, so if a file is data.bz2 this can bring it to data
- tar - (tape archive) create, extract, or manipulate .tar archives. -x extracts files from an archive, -f specifies the filename of the archive
Directory
- /tmp - temporary directory, used for storing filing created by applications, users, or the system temporarily, often will be deleted automatically or upon restart.
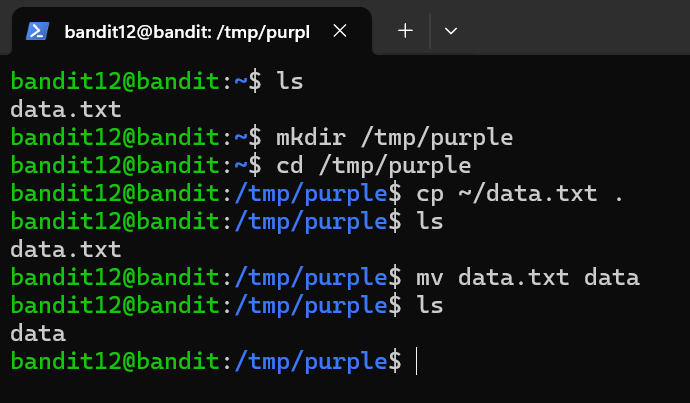
- First, we created a new directory named purple inside /tmp directory.
- Then, we cd into the new directory, and copy the data.txt file from the home directory ( ~ ) to the current directory, which brings the file into /tmp/purple.
Command: mv renames data.txt to data, we did this to remove the .txt extension from this file which is not a text file.
- Hex Dumps - each byte reprresents an 8-bit value from the original binary data, displayed in hexadecimal notation, it represents compressed data. For example, 1F8B indicates a Gzip compressed file. 425A and BZH signifies a Bzip2 compressed file. This would be helpful to know when utilizing a script that can automatically perform the decompression steps, many of the following commands are tied together in bash scripts to repeat future inputs.
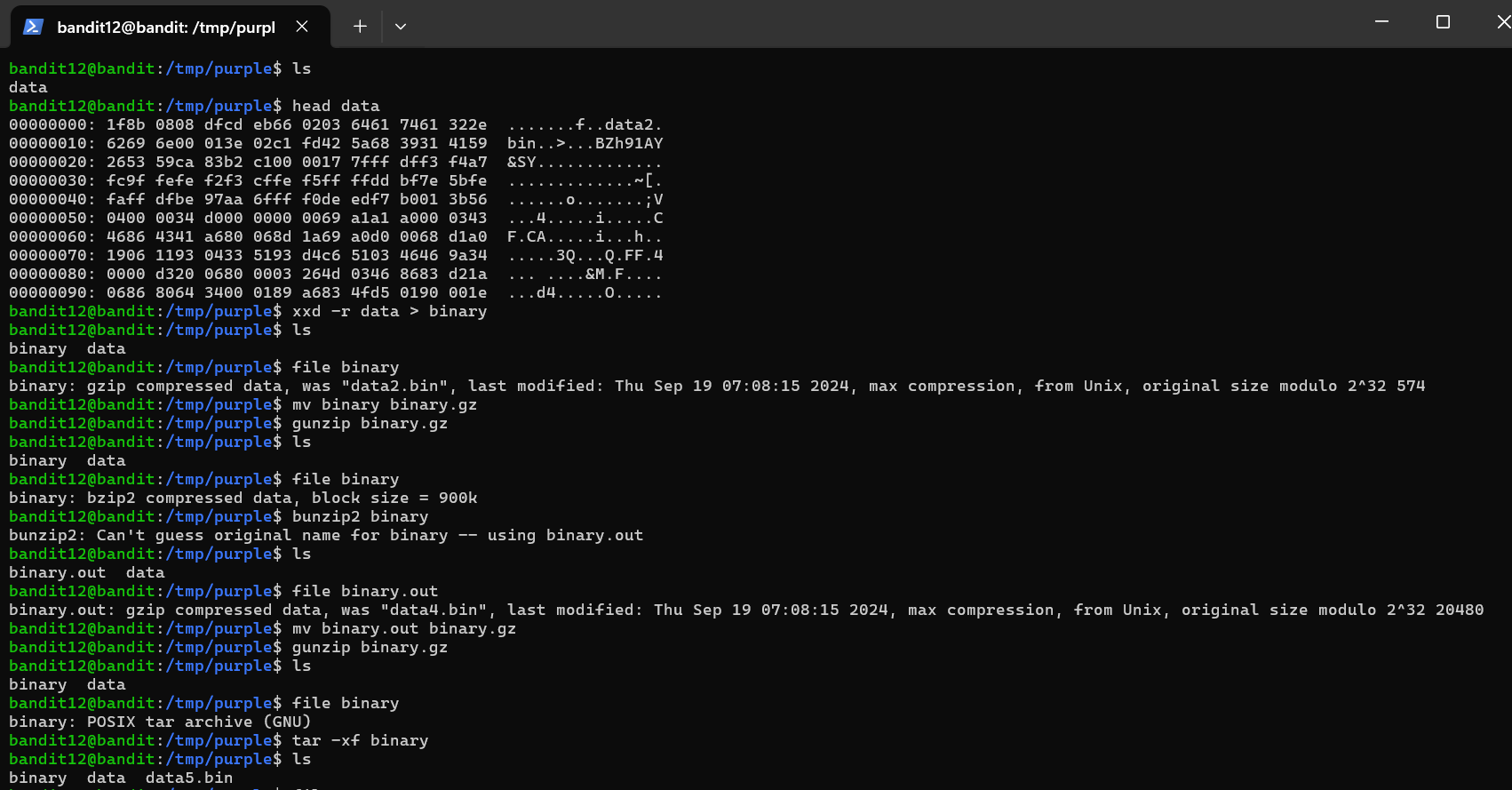
The purpose behind this level is to unravel the ‘tarball’ and get to the root of it which is the plaintext password. You may change directory names and files to what you’d like, good idea to remove old ones.
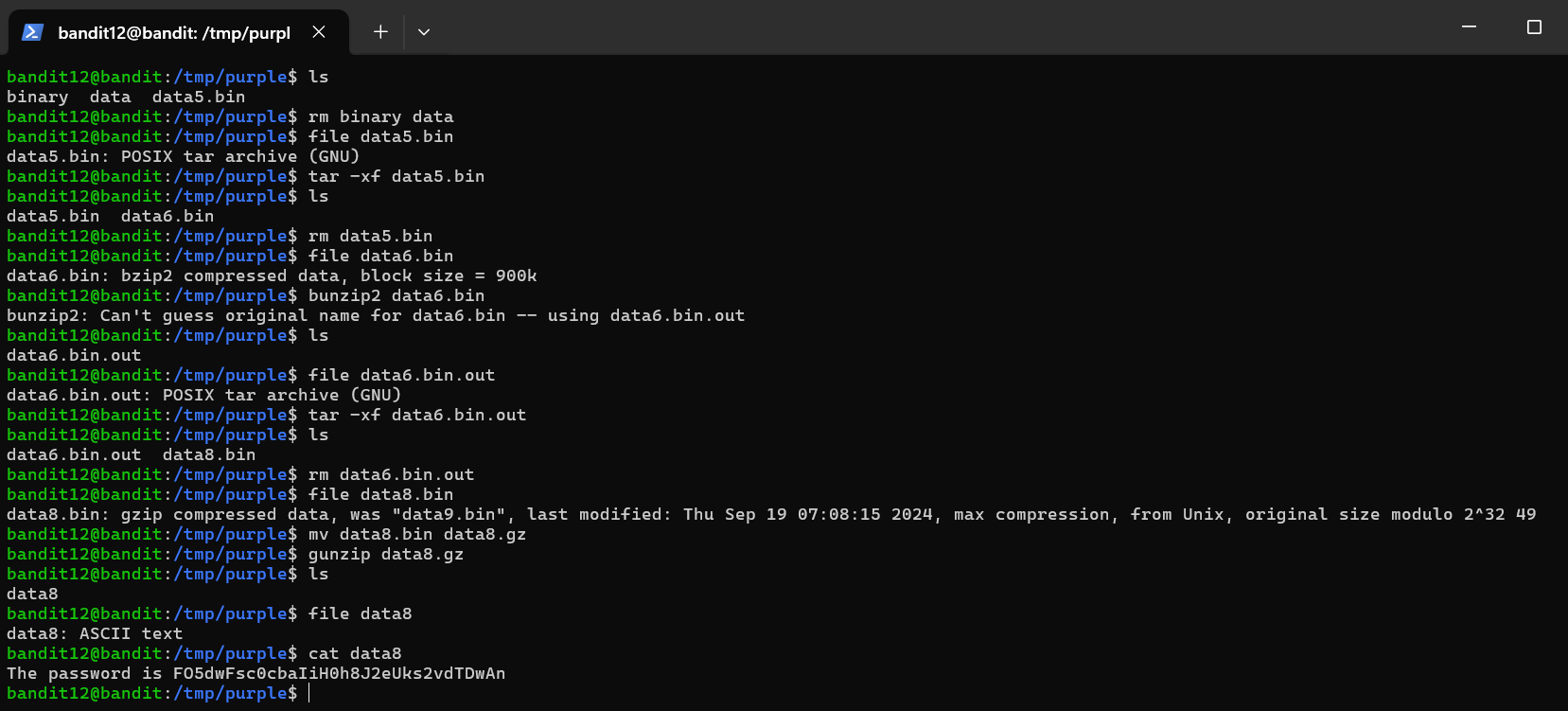
Tarball is a common term for compressed archive files. It combines multiple files and directories into a single file, making it easier to distribute, back up, and transfer.
Level Password: FO5dwFsc0cbaIiH0h8J2eUks2vdTDwAn